TheTruthSpy, a name that whispers intrigue and raises eyebrows, delves into the complex world of mobile phone monitoring software. It’s a tool with the potential to be both incredibly helpful and deeply problematic, depending entirely on its use. This exploration navigates the functionality, legal implications, and ethical considerations surrounding this powerful technology, examining its features, user experience, and the potential for misuse.
We’ll unpack the technical aspects, delve into data privacy concerns, and explore the various pricing models and customer support options available. Ultimately, we aim to provide a comprehensive overview, empowering you to make informed decisions about TheTruthSpy and similar technologies.
TheTruthSpy Functionality

TheTruthSpy software is a mobile monitoring application designed to track various activities on a target device. It offers a range of features aimed at providing comprehensive surveillance capabilities, though its ethical implications should always be carefully considered before use. Understanding its functionality is key to assessing its potential benefits and drawbacks.The core functionality of TheTruthSpy revolves around discreetly monitoring a target device’s activities.
This includes tracking location data, accessing call logs, monitoring text messages, and viewing social media activity. Beyond this, it often provides access to other data points, allowing users to build a detailed picture of the device’s usage. However, the specific features available can vary depending on the subscription level and the operating system of the target device.
Core Features of TheTruthSpy Software
TheTruthSpy boasts a robust feature set designed to provide comprehensive monitoring. Key features typically include GPS location tracking, enabling users to pinpoint the device’s location in real-time or review historical location data. Call logs are meticulously recorded, including timestamps, call duration, and phone numbers. Similarly, text messages are captured, providing access to both sent and received messages. Many versions also offer access to social media activity, browsing history, and even the ability to remotely control certain aspects of the target device.
The level of access granted varies between versions and subscriptions.
Comparison with Competitor Software
TheTruthSpy occupies a space in the mobile monitoring market alongside several competitors. While direct feature-by-feature comparisons are difficult due to the constantly evolving nature of these applications and the varying levels of access offered by different subscription plans, some general observations can be made. Competitors like mSpy and FlexiSPY offer similar core features, but may differ in their user interface, pricing structure, and the level of technical expertise required for installation and use.
Some competitors might excel in specific areas, such as advanced data extraction or remote control capabilities, while others may focus on ease of use and a simpler interface. The choice often depends on the specific needs and technical proficiency of the user.
Pros and Cons of Using TheTruthSpy
| Feature | Pro | Con | Overall Assessment |
|---|---|---|---|
| Comprehensive Monitoring | Provides a wide range of data points for a detailed overview of device activity. | Can be overwhelming for users and may lead to information overload. | High |
| Real-time Tracking | Allows for immediate awareness of device location and activity. | Requires constant monitoring and can be intrusive. | Moderate |
| Discreet Operation | Designed to operate in the background without alerting the user. | Raises ethical concerns regarding privacy and consent. | Low |
| Remote Access | Allows for management and control of the target device remotely. | Potential for misuse and unauthorized access. | Moderate |
| Pricing | Various subscription options cater to different budgets and needs. | Can be expensive depending on the chosen features and duration. | Moderate |
Legal and Ethical Implications
Using phone monitoring software like TheTruthSpy raises significant legal and ethical concerns. Its capabilities, while potentially useful in specific circumstances, can easily be misused, leading to serious consequences for both the user and the person being monitored. Understanding the legal framework and ethical considerations is crucial before even considering employing such technology.The legality of using TheTruthSpy varies drastically depending on your location.
In some jurisdictions, installing and using monitoring software without the explicit consent of the phone’s owner is strictly illegal and can result in hefty fines or even imprisonment. Laws regarding data privacy and surveillance differ significantly between countries, states, and even municipalities. For example, some European countries have incredibly strict data protection laws, while others have more lenient regulations.
Before considering using any monitoring software, you must research the specific laws in your area and the area where the target phone is being used. Ignoring these legal ramifications can lead to serious legal trouble.
Jurisdictional Variations in Legality
The legal landscape surrounding mobile phone monitoring is complex and fragmented. In the United States, for instance, laws vary by state. While some states have explicit laws addressing the issue, others rely on broader statutes concerning privacy violations and wiretapping. Similarly, in the European Union, the General Data Protection Regulation (GDPR) plays a significant role in defining the permissible limits of data collection and surveillance.
The GDPR, with its emphasis on data subject rights and consent, creates a high hurdle for the use of monitoring software. In many other countries, the legal framework might be less defined, making the legal implications even more uncertain. A thorough understanding of the specific legal requirements in each relevant jurisdiction is absolutely paramount.
Ethical Considerations of Mobile Phone Monitoring, Thetruthspy
Beyond the legal aspects, employing mobile phone monitoring software like TheTruthSpy presents a multitude of ethical dilemmas. The core issue revolves around the fundamental right to privacy. Secretly monitoring someone’s phone activity is a blatant violation of their privacy, regardless of the perceived justification. Trust and consent are paramount in any interpersonal relationship, and using such software undermines this trust, potentially causing irreparable damage to relationships.
Furthermore, the potential for misuse is significant; the software could be used for stalking, harassment, or blackmail, turning it into a tool for malicious intent.
Ethical Dilemmas Associated with TheTruthSpy
The use of TheTruthSpy presents several potential ethical dilemmas.
- Violation of privacy: Secretly monitoring someone’s communications and activities is a direct breach of their privacy and trust.
- Lack of consent: Using TheTruthSpy without the informed consent of the individual being monitored is ethically questionable.
- Potential for misuse: The software can be easily used for malicious purposes, such as stalking, harassment, or blackmail.
- Erosion of trust: The discovery of such monitoring can severely damage personal relationships and erode trust.
- Unintended consequences: The information gathered might be misinterpreted or used in ways that cause harm to the monitored individual.
User Experience and Interface
TheTruthSpy’s user interface is a key aspect of its overall effectiveness. A poorly designed interface can hinder even the most powerful monitoring capabilities, making the software frustrating and ultimately unusable. Conversely, a user-friendly interface can significantly enhance the overall experience, even for those unfamiliar with technical applications. This section will delve into the specifics of TheTruthSpy interface and its usability, comparing it to competitors.TheTruthSpy aims for a relatively straightforward design.
The dashboard typically presents a summarized view of monitored data, offering quick access to key information like recent calls, messages, and location updates. Navigation is generally intuitive, with clearly labeled menus and sections guiding users through the various features. However, the level of complexity increases as users delve into more advanced features, potentially presenting a steeper learning curve for less tech-savvy individuals.
The software’s overall design prioritizes functionality over visual aesthetics, resulting in a utilitarian, rather than visually appealing, interface.
User Feedback on TheTruthSpy’s Usability
User reviews regarding TheTruthSpy’s usability are mixed. While many praise the software’s functionality and the breadth of data it collects, some users express frustration with the interface’s occasional clunkiness and lack of intuitive design. For example, some users have reported difficulty navigating certain menus, particularly when dealing with advanced settings or large volumes of data. Others have commented on the lack of visual cues and helpful prompts, leading to a steeper learning curve than anticipated.
Positive feedback frequently focuses on the effectiveness of the data presentation and the overall ease of accessing core monitoring functions. These reviews suggest that while the software is functional, improvements in user interface design could significantly enhance user satisfaction.
Comparative Analysis of User Experience
Compared to competitors like mSpy and FlexiSPY, TheTruthSpy occupies a middle ground in terms of user experience. mSpy is generally regarded as having a more polished and visually appealing interface, with a greater emphasis on user-friendliness. FlexiSPY, on the other hand, often boasts more advanced features but with a correspondingly more complex interface, making it less accessible to casual users.
TheTruthSpy’s interface falls somewhere between these two extremes: it’s functional but not as polished as mSpy, and less complex than FlexiSPY. The choice between these platforms ultimately depends on the user’s priorities: a seamless, intuitive experience versus access to a broader range of features. For users prioritizing ease of use, mSpy might be preferred, while those needing highly specialized features might opt for FlexiSPY despite its steeper learning curve.
TheTruthSpy offers a compromise, providing a balance between functionality and user-friendliness.
Technical Aspects and Security
TheTruthSpy’s functionality relies on a complex interplay of client-side applications installed on the target device and a server-side infrastructure that manages data collection, storage, and user access. Understanding its technical architecture is crucial for assessing its security implications and potential vulnerabilities.The software’s client-side component operates in the background of the target device, collecting data according to the user’s specifications.
This data is then transmitted to TheTruthSpy’s servers using various methods, depending on the target device’s capabilities and network connectivity. The server-side infrastructure is responsible for storing and organizing this data, providing a web interface for users to access and manage their monitoring activities. The architecture incorporates several layers of security, though their effectiveness is debatable.
Technical Architecture
TheTruthSpy likely utilizes a multi-tiered architecture. The client-side application interacts with a mobile device’s operating system (Android or iOS) to access and collect data. This data is then transmitted to intermediary servers, potentially using techniques like HTTPS for secure communication. These intermediary servers may handle load balancing and data routing before the information reaches the main database servers where the data is stored.
Finally, a web application provides the user interface for accessing and managing the collected information. The exact specifics of the architecture are proprietary and not publicly available.
Potential Security Vulnerabilities
Several potential security vulnerabilities exist within TheTruthSpy’s architecture. Data transmitted between the client and server could be intercepted by a sophisticated attacker using techniques like man-in-the-middle attacks. The security of the database servers themselves is paramount; a breach could expose a large amount of sensitive user and target data. Additionally, vulnerabilities in the client-side application could allow attackers to gain unauthorized access to the target device or disable the monitoring functionality.
The lack of transparency surrounding the software’s security measures increases the risk of unknown vulnerabilities. The complexity of the software and the constant evolution of hacking techniques present an ongoing challenge.
Data Encryption Methods
TheTruthSpy’s documentation often claims to employ various encryption methods to protect user data. However, the specifics of these methods are generally not publicly disclosed, making independent verification difficult. They may use SSL/TLS for communication between the client and server, potentially encrypting data in transit. However, the encryption used for data at rest (stored on the servers) is unclear and could be weaker.
Without independent audits and detailed disclosure of encryption algorithms and key management practices, the actual level of data security remains questionable. A lack of transparency in this area raises significant concerns about the security of sensitive information.
Installation and Setup Process
Getting TheTruthSpy up and running involves a few key steps. The entire process, while requiring some technical understanding, is designed to be relatively straightforward. Remember to always adhere to the legal and ethical implications discussed earlier before proceeding.
The installation process differs slightly depending on the target device’s operating system (Android or iOS). However, the core principles remain the same: gaining access to the device, downloading the app, and configuring the settings. Successful installation hinges on having physical access to the target device for a short period and understanding the specific requirements for each OS.
Android Device Installation
Installing TheTruthSpy on an Android device typically involves downloading the APK file and installing it manually. This requires enabling the “Unknown Sources” setting in the device’s security settings to allow installation from sources other than the Google Play Store. After installation, you’ll need to configure the app with the credentials provided during the purchase process. The app then runs in the background, invisibly monitoring the device’s activity.
iOS Device Installation
Installing TheTruthSpy on an iOS device is a more complex process and often requires jailbreaking the device. Jailbreaking circumvents Apple’s security restrictions, allowing the installation of third-party apps. This process is risky and could void the device’s warranty. Once jailbroken, the TheTruthSpy app can be installed and configured similarly to the Android version. However, it’s crucial to understand that jailbreaking is a significant undertaking and may render the device unstable or vulnerable to other security risks.
Thoroughly research the implications before proceeding.
Best Practices for Successful Installation
Several best practices can improve the likelihood of a smooth and successful installation. These practices focus on minimizing errors and ensuring the app functions correctly.
- Ensure a stable internet connection on both the target device and the monitoring device during the installation and configuration processes.
- Carefully follow the provided instructions specific to the target device’s operating system (Android or iOS).
- Before installing, back up the target device’s data to prevent data loss in case of unforeseen issues.
- Regularly check for updates to TheTruthSpy to ensure optimal performance and security.
- If encountering problems, refer to the app’s support documentation or contact customer support for assistance.
Configuring TheTruthSpy Settings
Once installed, TheTruthSpy’s settings need to be configured to specify the type of data to monitor. This allows you to tailor the monitoring to your specific needs, selecting features such as call logs, SMS messages, GPS location, social media activity, and more. It is crucial to understand the implications of monitoring each data type before enabling it.
- Call Logs: Enables the monitoring of incoming and outgoing calls, including timestamps and phone numbers.
- SMS Messages: Allows the monitoring of text messages, including content, sender, and recipient information.
- GPS Location: Tracks the real-time location of the target device.
- Social Media Activity: Monitors activity on various social media platforms (depending on app capabilities and platform compatibility).
- Surroundings Recording: This feature, if available, allows for the recording of ambient sounds around the target device.
Remember to carefully review and adjust these settings based on your requirements and ethical considerations. Incorrectly configured settings might lead to data overload or missed crucial information.
Data Privacy and User Data
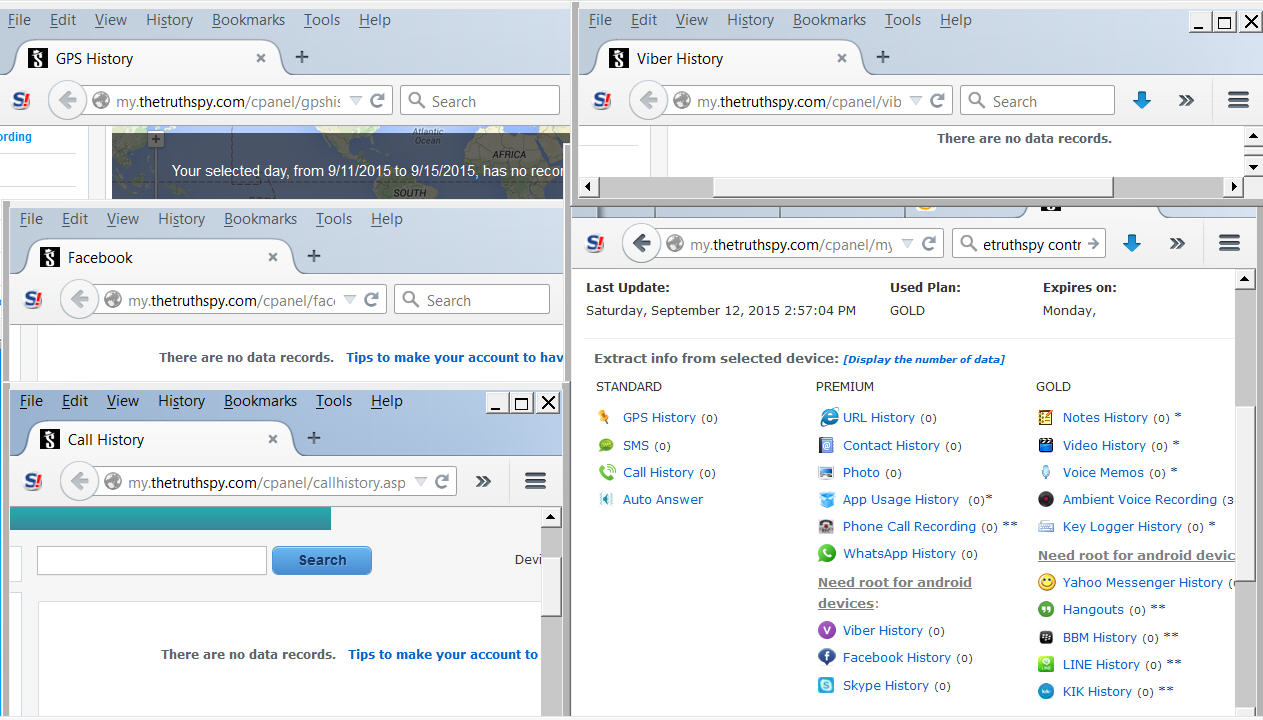
TheTruthSpy, like any monitoring software, raises significant concerns regarding data privacy and the handling of user data. Understanding the types of data collected, how it’s stored, and for how long is crucial for assessing the potential risks and ethical implications associated with its use. This section details TheTruthSpy’s data collection and retention practices.TheTruthSpy collects a wide range of data from the target device.
This typically includes, but is not limited to, GPS location data, call logs (including numbers and timestamps), text messages (both sent and received), social media activity (depending on app permissions), browsing history, photos and videos, and even keystrokes (depending on the specific features enabled). The exact data collected depends on the features activated by the user and the operating system of the target device.
The volume of data can be substantial, particularly over extended monitoring periods.
Types of Data Collected by TheTruthSpy
TheTruthSpy’s data collection practices encompass various categories of personal information. This includes location data, providing precise coordinates of the target device; communication data, such as call logs, SMS messages, and instant messaging interactions; multimedia data, consisting of photos, videos, and audio recordings; and application usage data, documenting which apps are used and for how long. Additionally, some versions might capture keystrokes, offering a detailed record of typing activity.
The specific data points collected are subject to the features enabled within the app.
TheTruthSpy’s Data Storage and Retention Policies
TheTruthSpy’s data storage and retention policies are typically not explicitly detailed in their public documentation, often necessitating careful examination of their terms of service and privacy policy. Generally, the collected data is stored on TheTruthSpy’s servers, with the retention period varying based on user settings and subscription plans. Some plans might offer longer data storage periods than others. It is crucial to understand that the longer data is stored, the greater the risk of data breaches or unauthorized access.
Users should be aware of the potential for indefinite data retention unless specific actions are taken to delete the data.
Data Flow within the TheTruthSpy System
The data flow within TheTruthSpy can be visualized as follows:
Imagine a flowchart. Box 1: Target Device. Arrows point from Box 1 to Box 2: TheTruthSpy App. Arrows point from Box 2 to Box 3: TheTruthSpy Servers. Arrows point from Box 3 to Box 4: User Dashboard (accessed via web browser or app).
Box 5: Data Deletion (initiated by user). Arrows point from Box 3 to Box 5. The arrows represent the flow of data. Data from the target device is collected by the TheTruthSpy app, transmitted to TheTruthSpy’s servers, and then made accessible to the user through their online dashboard. The user can also initiate data deletion, removing the data from the servers.
This simplified model omits the complexities of data encryption, security protocols, and potential intermediary servers.
Pricing and Subscription Models
TheTruthSpy, like many monitoring applications, offers tiered subscription plans to cater to different needs and budgets. Understanding these plans and their associated features is crucial before making a purchase decision. This section details the various pricing options and the functionalities included in each tier. We’ll also compare TheTruthSpy’s pricing to that of its competitors.
TheTruthSpy’s pricing structure is generally based on the length of the subscription and the features included. Longer subscriptions usually offer a lower monthly cost per month. The features offered vary significantly between the basic and premium plans, affecting the overall price. It’s important to carefully evaluate your monitoring needs to determine which plan best suits your requirements and budget.
TheTruthSpy Pricing Plans
TheTruthSpy typically offers at least two subscription tiers: a basic plan and a premium plan. The basic plan usually provides core monitoring features, while the premium plan unlocks more advanced capabilities. Specific features and pricing can vary, so it’s always recommended to check TheTruthSpy’s official website for the most up-to-date information. However, a common structure might include features such as call logs, text message monitoring, and GPS location tracking in the basic plan, with premium plans adding social media monitoring, keylogging, and application usage tracking.
Prices generally range from a few dollars per month for the basic plan to significantly more for the premium plan. The exact pricing varies based on the length of the subscription, with longer subscriptions typically offering a discount per month.
Feature Comparison Across Subscription Tiers
The following table illustrates a typical feature comparison between the basic and premium plans. Note that this is a general representation, and actual features and pricing may vary depending on the current offerings on TheTruthSpy’s website. Always consult the official website for the most accurate and up-to-date information.
| Feature | Basic Plan | Premium Plan |
|---|---|---|
| Call Logs | Yes | Yes |
| Text Messages | Yes | Yes |
| GPS Location Tracking | Yes | Yes (with enhanced accuracy) |
| Social Media Monitoring (e.g., WhatsApp, Facebook) | No | Yes |
| Keylogging | No | Yes |
| Application Usage Monitoring | No | Yes |
| Screenshot Capture | No | Yes |
| Surrounding Recording | No | Yes (May have legal restrictions) |
TheTruthSpy Pricing Compared to Competitors
Comparing TheTruthSpy’s pricing to competitors is crucial for determining value. The market offers various monitoring software options, each with its own pricing structure and feature set. Direct price comparison can be challenging because features and plans can vary widely. However, a general comparison is presented below. Remember that prices can fluctuate, so always check the official websites for the most current pricing information.
| Software | Basic Plan Price (USD/Month – Example) | Premium Plan Price (USD/Month – Example) | Features Included (Example) |
|---|---|---|---|
| TheTruthSpy | $29.99 | $49.99 | Call logs, texts, GPS, basic social media monitoring (some platforms) |
| Competitor A | $25.00 | $55.00 | Call logs, texts, GPS, keylogging, app usage |
| Competitor B | $35.00 | $65.00 | Call logs, texts, GPS, social media, screen recording |
Customer Support and Resources
TheTruthSpy’s customer support is a crucial aspect of its overall service, influencing user satisfaction and the effectiveness of the software. A robust and responsive support system is essential for addressing technical issues, resolving billing disputes, and answering user queries. The availability and quality of these resources directly impact the user experience and overall perception of the product.The effectiveness of TheTruthSpy’s customer support is a mixed bag, according to available online reviews.
While some users report positive experiences with prompt and helpful responses, others describe difficulties in contacting support or receiving inadequate assistance. This disparity highlights the need for a more consistent and reliable support structure.
Available Support Channels
TheTruthSpy typically offers support through a few key channels. These usually include email support, which is often the primary method of contact. Some users have also reported the availability of live chat, though its consistency across different platforms or time periods is unclear. A comprehensive FAQ section on their website is also often cited, offering solutions to common problems.
However, the absence of a readily available phone support option limits accessibility for users who prefer immediate verbal assistance.
User Reviews and Testimonials on Customer Service
Online reviews present a varied picture of TheTruthSpy’s customer service. Positive feedback frequently mentions helpful email responses and solutions provided by support staff. Users who received timely and effective assistance often praise the knowledge and professionalism of the support team. However, negative reviews highlight significant delays in receiving responses, unhelpful or generic replies, and a lack of personalized support.
Some users report difficulty in resolving their issues, even after multiple attempts to contact support. The inconsistency in reported experiences suggests room for improvement in the standardization and efficiency of their customer support processes. The overall sentiment appears to lean towards a need for more consistent and proactive support.
Target Audience and Use Cases
TheTruthSpy, like any monitoring software, caters to a specific audience with particular needs. Understanding its legitimate uses is crucial to responsibly discussing its potential applications and ethical considerations. Misuse, however, is a serious concern and should be addressed alongside legitimate applications.The primary target audience for TheTruthSpy consists of parents, employers, and individuals with specific security concerns. Each group has unique reasons for considering such monitoring software, and these reasons often fall within legally and ethically acceptable boundaries.
However, it’s vital to remember that the line between acceptable and unacceptable use can be blurry, and careful consideration is always necessary.
Legitimate Use Cases for TheTruthSpy
TheTruthSpy can be a valuable tool in certain situations where monitoring is necessary for the safety and well-being of individuals or to protect business interests. These scenarios often involve a pre-existing relationship of trust and responsibility, such as that between parent and child or employer and employee.
- Parental Control: Parents might use TheTruthSpy to monitor their children’s online activity, protecting them from cyberbullying, inappropriate content, or online predators. This can be particularly useful for younger children or teenagers who may not fully understand the risks of the internet.
- Employee Monitoring: In some industries, such as those handling sensitive data or financial transactions, employers might use TheTruthSpy to monitor employee activity to ensure compliance with company policies, prevent data breaches, and maintain workplace security. This should, however, always be done transparently and with the knowledge and consent of the employee, ideally Artikeld in employment contracts.
- Personal Security: Individuals may use TheTruthSpy to monitor their own devices in the event of theft or suspected unauthorized access. This allows for tracking the device’s location and potentially identifying the perpetrator.
Inappropriate and Unethical Use Cases for TheTruthSpy
The misuse of TheTruthSpy can lead to serious ethical and legal ramifications. It is crucial to understand that this software should never be used to violate someone’s privacy without their knowledge or consent.
- Spying on a Partner or Spouse: Using TheTruthSpy to monitor a partner’s activities without their knowledge or consent is a serious breach of trust and could have severe legal and emotional consequences. This constitutes a violation of privacy and potentially harassment.
- Stalking or Harassment: Using TheTruthSpy to track someone’s location or monitor their communications without their consent is a form of stalking and harassment, which is illegal and morally reprehensible.
- Unauthorized Monitoring of Employees: Using TheTruthSpy to monitor employees without their knowledge or consent, especially in situations where it is not explicitly stated in employment contracts or justified by legitimate business needs, is a violation of privacy and could lead to legal action.
- Illegal Activities: Using TheTruthSpy to assist in illegal activities, such as blackmail or extortion, is a serious crime and carries severe penalties.
Alternative Solutions and Comparisons
TheTruthSpy isn’t the only game in town when it comes to mobile monitoring software. Several alternatives exist, each with its own strengths and weaknesses. Understanding these alternatives allows for a more informed decision based on specific needs and priorities. This section will compare TheTruthSpy to other popular solutions and explore alternative methods for achieving similar monitoring goals.
Okay, so TheTruthSpy is, like, totally intense for monitoring stuff, right? But imagine if you used that kind of detailed tracking to analyze how users interact with an animation you made in adobe animate. You could get crazy specific data on user behavior to improve your designs, almost like reverse-engineering their experience with TheTruthSpy’s level of detail, but for, you know, good.
It’s all about data analysis in the end.
Comparison with Other Mobile Monitoring Solutions
Several competitors offer similar functionality to TheTruthSpy, including mSpy, FlexiSPY, and Spyic. These apps typically provide features such as call logs monitoring, SMS tracking, GPS location tracking, social media monitoring, and keylogger capabilities. However, they differ in their pricing, feature sets, ease of use, and level of technical expertise required for installation and operation. For example, FlexiSPY might offer more advanced features but demands a higher level of technical knowledge, while mSpy might be more user-friendly but offer fewer sophisticated tracking options.
TheTruthSpy’s position within this competitive landscape is determined by its pricing strategy, the specific features it emphasizes, and its overall user experience. A direct comparison across these platforms would require a detailed feature-by-feature analysis, including a consideration of any limitations or potential vulnerabilities.
Alternative Methods for Achieving Similar Monitoring Goals
Beyond dedicated mobile monitoring software, there are alternative approaches to achieving similar monitoring goals. These methods often involve using built-in device features or leveraging third-party apps with more limited monitoring capabilities. For instance, parental control apps like Google Family Link offer location tracking and app usage monitoring, but lack the comprehensive surveillance capabilities of TheTruthSpy. Similarly, using a phone’s built-in location sharing features allows for tracking, but only if the target user actively enables and maintains this sharing.
These alternatives offer less comprehensive monitoring but often come with greater transparency and less potential for privacy violations. The trade-off is a reduction in the scope of monitoring capabilities.
Advantages and Disadvantages of Alternative Solutions
The choice between TheTruthSpy and alternative solutions hinges on a cost-benefit analysis. Dedicated mobile monitoring software like TheTruthSpy provides extensive tracking capabilities, but this comes at the cost of higher pricing and potential privacy concerns. Alternatively, using built-in features or less comprehensive apps offers greater transparency and reduced cost, but significantly limits the scope of monitoring. Parental control apps provide a middle ground, offering moderate monitoring capabilities with a focus on child safety and often incorporating educational features.
The decision of which solution to use ultimately depends on the specific monitoring needs, the ethical considerations involved, and the user’s technical expertise. A thorough understanding of the advantages and disadvantages of each approach is crucial for making an informed choice.
Last Recap
So, is TheTruthSpy a helpful tool or a privacy nightmare? The answer, like so many things in life, is nuanced. While it offers legitimate uses for concerned parents or employers, the potential for misuse and the ethical gray areas it inhabits cannot be ignored. Ultimately, responsible use and a thorough understanding of the legal and ethical implications are paramount.
This deep dive hopefully provides the information needed to navigate this complicated landscape responsibly.
FAQ Guide
Is TheTruthSpy undetectable?
No monitoring software is completely undetectable. Sophisticated users can find ways to identify and disable it. The level of detectability often depends on the target device’s operating system and the user’s technical skills.
What happens if the target phone changes its SIM card?
The effectiveness of TheTruthSpy can be impacted by a SIM card change. Some features might be disrupted, requiring re-installation or adjustments to the monitoring setup.
Can I use TheTruthSpy on an iPad or tablet?
TheTruthSpy’s compatibility with iPads and tablets varies depending on the specific version and features. Check their official documentation for device compatibility before purchasing.
What are the penalties for illegally using TheTruthSpy?
Penalties for illegal use vary widely by jurisdiction and the specific laws violated. This could range from fines to imprisonment, depending on the severity and nature of the misuse.
